Running a WooCommerce store means you’re already dealing with a lot of moving parts.
One of the biggest challenges? Keeping your store secure.
WooCommerce’s popularity makes it a prime target for fraudsters, and carding attacks are one of the most common threats.
In a carding attack, bots are used to test stolen credit card details by making small purchases on your site.
These attacks can lead to extra transaction fees, chargebacks, and even damage to your reputation.
In this guide, we’ll walk you through six practical tips to help you prevent WooCommerce carding attacks and protect your store from fraud.
Table of Contents
- 1 What Are WooCommerce Carding Attacks and How Do They Work?
- 2 Why WooCommerce Sites Are Prime Targets for Carding Attacks
- 3 How Do Carding Attacks Impact WooCommerce Sites?
- 4 How to Identify a Card Testing Attack on Your WooCommerce Site?
- 5 6 Proven Strategies to Prevent WooCommerce Carding Attacks
- 5.1 1. Enable CAPTCHA or reCAPTCHA on checkout pages
- 5.2 2. Use an address verification system (AVS) and 3D secure authentication
- 5.3 3. Implement rate-limiting on transactions
- 5.4 4. Set up anti-fraud plugins for WooCommerce
- 5.5 5. Require account creation for checkout
- 5.6 6. Monitor server-side indicators and set up alerts
- 6 Strengthen WooCommerce Security with These 4 Advanced Techniques
- 7 What to Do If a WooCommerce Site Is Under a Carding Attack?
- 8 Wrapping Up: Secure Your WooCommerce Store from Carding Attacks
What Are WooCommerce Carding Attacks and How Do They Work?
A WooCommerce carding attack is a cyberattack in which hackers attempt to test large numbers of stolen or randomly generated credit card details on a WooCommerce-powered eCommerce site.
These attackers aim to verify which cards are active by making small purchases or orders. If a card works, they may exploit it further, such as selling information on the dark web, making multiple purchases, etc.
To understand how this can look in real life, imagine you run an online clothing store.
Suddenly, you notice a sudden spike in tiny transactions, around $050 to $0.90 each, coming from various locations and zones.
Although each transaction fails, your store is still charged fees for each attempt.
After investigating, you find a bot testing your site with stolen credit card details using the WooCommerce checkout page.
Also, your site is not protected with basic security like CAPTCHA and rate-limiting.
This scenario is a classic example of a WooCommerce carding attack.
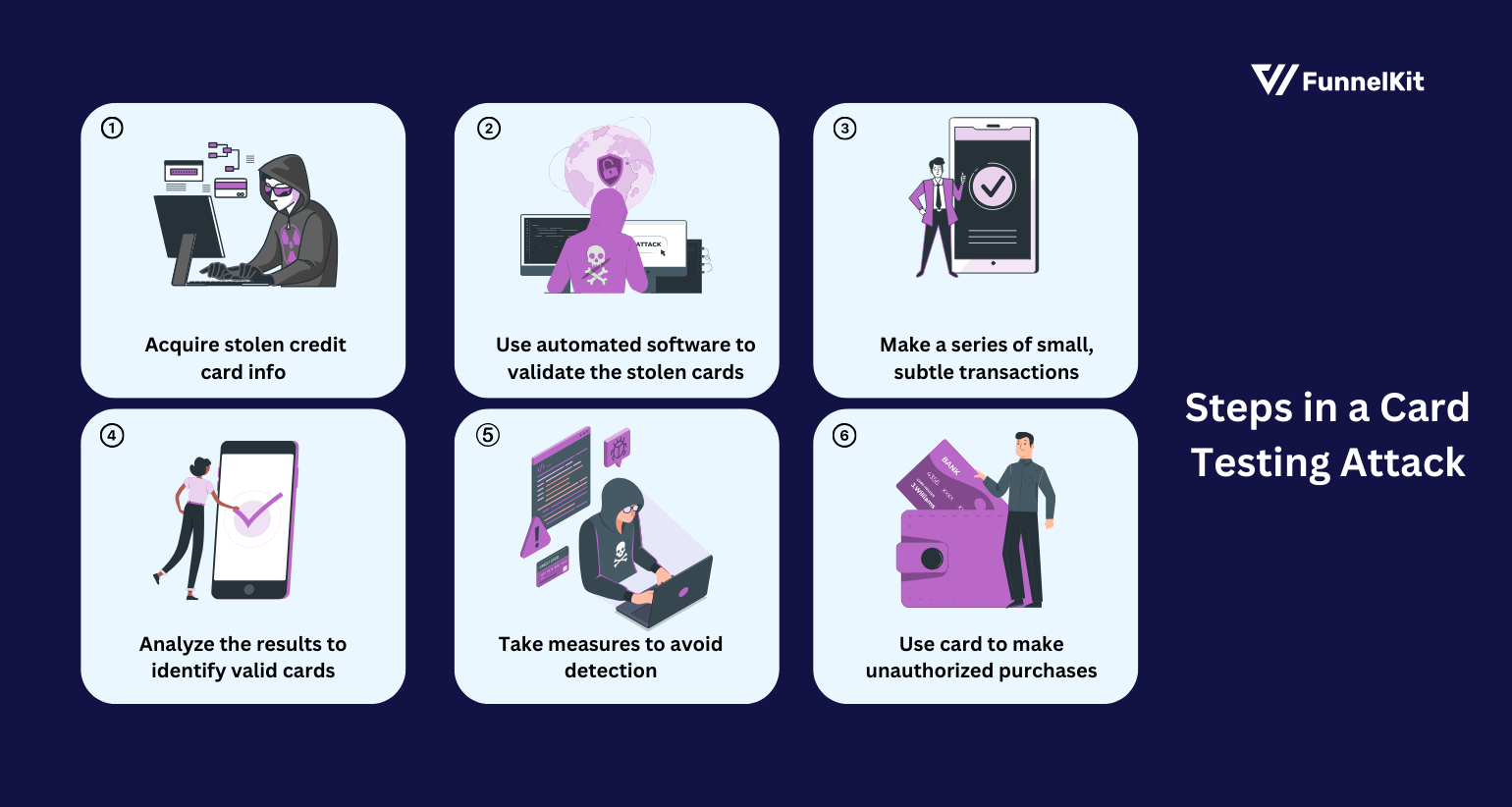
Here’s the step of how attackers run the carding testing on a WooCommerce store.
- Step 1: Acquire stolen credit information
- Step 2: Use automated software to validate the stolen cards
- Step 3: Make a series of small, subtle transactions
- Step 4: Analyze the results to identify valid cards
- Step 5: Take measures to avoid detection
- Step 6: Use the card to make unauthorized purchases
Why WooCommerce Sites Are Prime Targets for Carding Attacks
WooCommerce is a popular eCommerce platform for WordPress, with over 8 million active users and a 20.1% market share among eCommerce sites, according to MobiLoud.
Having this vast traffic, WooCommerce may lack some advanced security measures for incidents like carding test attacks.
Furthermore, WooCommerce stores can have different settings depending on the business type. Smaller stores usually don’t enable features like CAPTCHA, AVS (Address Verification System), or rate-limiting features, which can easily detect and block carding bots.
So, the attackers take advantage of this and continue their vulnerable activities in stores.
Apart from the discussed reasons, here are other reasons why WooCommerce sites face carding test attacks:
- Direct access to checkout and payment pages: WooCommerce sites process payments directly, often without multi-layered protections. This allows bots to test card information through repeated small transactions.
- Lower security awareness among small businesses: Many WooCommerce sites are run by small or medium-sized companies. These companies lack the security knowledge needed to prevent future vulnerabilities, making them easier targets for carding attempts.
- Lack of built-in anti-bot security: WooCommerce does not include comprehensive anti-bot tools by default. Site owners must purchase or rely on third-party plugins or custom security configurations. That’s why it’s often overlooked and opens vulnerabilities.
These are some common issues that cause a WooCommerce site to become a target for a carding attack.
How Do Carding Attacks Impact WooCommerce Sites?
Anything related to payment or purchase has a big impact on an online store. Nothing goes the opposite with the carding attack.
Your site is receiving unwanted traffic, untraceable transactions, and bot attacks; indeed, this incident is not expected for any store owners.
From hampering brand image to losing customer trust, the carding attack has a lot of harmful impacts on WooCommerce sites.
Here are five primary things that the carding attack can impact a WooCommerce store:
- Transaction fees: Each attempt, successful or not, incurs a processing fee. These fees quickly add up to significant costs for the store owner, mainly when hundreds or thousands of tests are performed.
- Lose money due to chargeback rates: Valid cardholders may dispute unauthorized transactions, resulting in chargebacks that are both costly and damaging to the store’s reputation with payment processors.
- Potential account suspension: Payment processors may temporarily suspend or even terminate a merchant’s account if they detect suspicious activity. This disrupts the store’s ability to process legitimate transactions.
- Reputational damage: Repeated fraudulent activity on a site can hamper customer trust. It discourages customers from visiting the shop and purchasing anything, resulting in the loss of some potential buyers.
- Increased security and compliance issues: Sites experiencing carding attacks may need to upgrade their security measures and face stricter compliance requirements, which can be costly and time-consuming.
Overall, carding attacks have serious implications for WooCommerce stores, impacting finances, reputation, and overall site security.
How to Identify a Card Testing Attack on Your WooCommerce Site?
Now you know what a carding attack is, why it targets WooCommerce stores, and its potential impact, let’s look at how to detect such attacks early.
An online store involves many transactions, customer details, and an extensive database. Thus, a single security compromise can escalate into a critical issue like a card testing attack or carding attack.
Early detection can mitigate financial losses and keep you in a safe spot. It also helps store owners take the required action to limit the initial risk factors.
You may wonder how you will know that your WooCommerce store is under a card testing attack. Right?
There are two main ways to identify this: from the server side and through WooCommerce purchase and order indications.
Method 1: Server-side indicators of a WooCommerce carding attack
Here are the server-side indications that point towards a potential carding attack:
- Increased requests from specific IP addresses
Carding bots typically generate a high volume of requests from specific IP addresses.
Monitoring server logs for repeated requests from specific IPs is one of the first signs of a carding attack.
- Slower website response times
A sudden spike in suspicious bot attacks results in massive traffic, though this is not organic traffic. So when these bots make rapid, repeated attempts at checkout, your entire server experiences an unusual load.
This may cause your website to respond more slowly than usual as the server struggles to handle the sudden increase in requests.
- Elevated server load
High volumes of bot requests can strain the server, leading to elevated load times. Monitoring for unusual spikes in server load helps detect potential bot attacks.
- Queueing of HTTP requests
As the server reaches capacity due to increased bot traffic, HTTP requests may queue up, delaying response times for real users. Server logs showing queued or delayed HTTP requests often indicate excessive bot activity targeting the checkout page.
Method 2: Purchase and order-related indicators for the carding attack in WooCommerce
Here are the purchase and order indicators to identify the carding attack in your WooCommerce store.
- Unusually high traffic to the checkout page
Carding bots often target the checkout page specifically, directing traffic. Monitoring server traffic patterns can help identify unusual spikes in checkout requests, a common sign of card testing.
- A sudden spike in failed transactions
A significant increase in transaction failures, especially small-value transactions, can indicate that bots are attempting to test large numbers of stolen credit card numbers.
- Frequent small transactions
Attackers often make low-value purchases (e.g., under $1) to check the validity of cards without drawing too much attention. Multiple small transactions from various regions or accounts may signal a carding attempt.
- Multiple transactions from the same IP address or location
If you notice multiple transactions or checkout attempts from a single IP address or a suspicious location, this is often a red flag for bot-driven carding attacks. You can also find the IP address-related details in the WooCommerce order section.
- Increased chargebacks and customer disputes
When validated cards are used for unauthorized purchases, affected cardholders may initiate chargebacks. A rise in chargebacks or disputes can indicate that some transactions have been tested or validated fraudulently on your site.
These are the general indicators that your WooCommerce site is under a carding attack. Identifying these signs allows you to mitigate the effects of the carding attack.
Now let’s talk about how to conduct the carding attack.
6 Proven Strategies to Prevent WooCommerce Carding Attacks
Proactive security measures are essential to protect your WooCommerce site from carding attacks.
Here are six practical strategies to help safeguard your WooPayments system from fraudulent activity:
1. Enable CAPTCHA or reCAPTCHA on checkout pages
CAPTCHA prevents bots from submitting multiple fraudulent transactions, as it requires human interaction to complete.
You can also integrate Google reCAPTCHA or WooCommerce Captcha on your checkout page to add an extra layer of security.
This simple addition makes it harder for bots to execute high volumes of card tests.

2. Use an address verification system (AVS) and 3D secure authentication
AVS and 3D Secure (3DS) are tools that payment processors provide to verify cardholder details. AVS checks the billing address, while 3DS requires an additional step for cardholder verification.
Enable AVS and 3D Secure through your payment processor's settings. AVS flags mismatched billing addresses, and 3DS adds two-factor authentication for further verification.
3. Implement rate-limiting on transactions
Rate-limiting restricts the number of transactions or checkout attempts a single user or IP address can make within a specific timeframe. Hence, it reduces the ability of bots to test large numbers of cards.
Use a WooCommerce security plugin or configure your server settings to limit transaction frequency, reducing the chance of automated attacks.
4. Set up anti-fraud plugins for WooCommerce
Anti-fraud plugins monitor transaction patterns, block suspicious transactions, and provide additional security checks tailored to prevent carding.
Consider plugins like WooCommerce Anti-Fraud or FraudLabs Pro, which can automatically flag or block high-risk transactions based on various criteria, such as IP address, geolocation, and transaction amount.
5. Require account creation for checkout
Forcing customers to create an account on checkout adds an extra step that bots struggle to bypass, and it also allows better tracking of legitimate customer behavior.
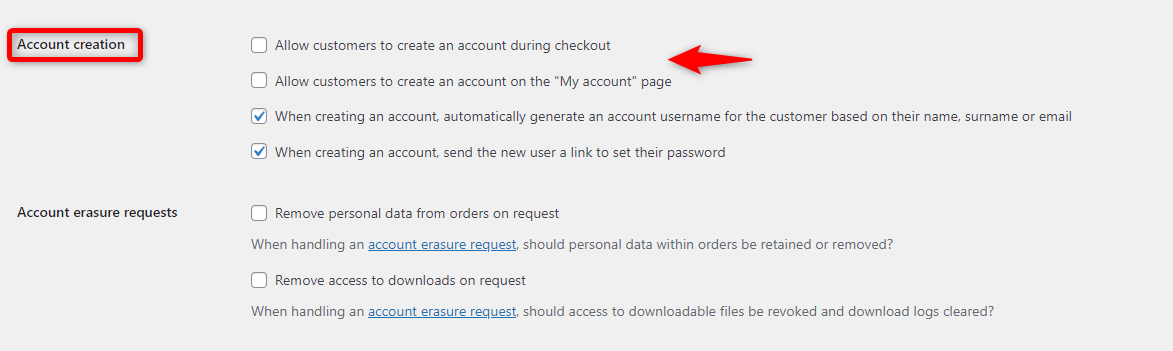
Configure your WooCommerce settings to require account registration at checkout. Though this adds a minor step for customers, it significantly reduces the risk of automated card testing by bots.
6. Monitor server-side indicators and set up alerts
Carding attacks often strain server resources, causing high traffic and unusual load on your checkout system.
Monitor server logs regularly for indicators like increased requests from specific IP addresses, slower response times, and HTTP request queuing. Setting up alerts for unusual server loads can help you respond quickly if an attack begins.
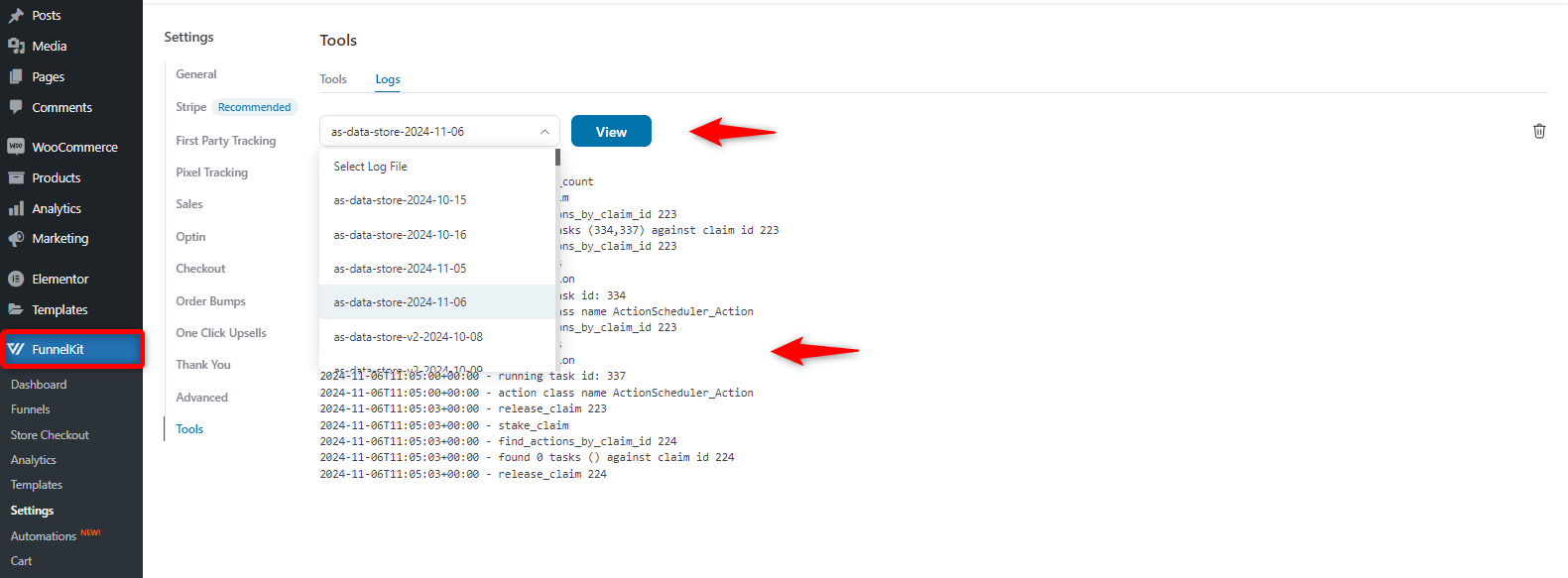
By the way, if you’re using the FunnelKit Funnel Builder to set up custom checkout pages, check the logs to ensure everything works smoothly.
Navigate to FunnelKit > Settings > Tools > Logs. You can sort out the log details from here.
These measures provide a solid defense against any bot attack or vulnerabilities. Plus, it protects your WooCommerce site from the additional costs and risks associated with WooPayments carding attacks.
By implementing these best practices, you can create a safer, more secure environment for your business and customers.
Here are some additional yet advanced tips that you can follow and apply.
Strengthen WooCommerce Security with These 4 Advanced Techniques
While basic security measures like CAPTCHA and anti-fraud plugins are essential, implementing advanced security techniques can further protect your WooCommerce store from any vulnerabilities, including carding attacks.
Here are five advanced methods to strengthen your WooCommerce security:
- Implement a web application firewall (WAF)
“Nearly 60% of WooCommerce stores use web application firewalls (WAFs) to filter traffic and block cyber threats, keeping their sites secure and running smoothly.”
A WAF is a barrier between your website and potential threats. It filters and monitors unusual HTTP traffic, detects and blocks malicious bot traffic, and protects your site from other common threats, such as SQL injection and cross-site scripting (XSS).
Many security providers, like Cloudflare and Sucuri, offer WAF solutions that integrate easily with WooCommerce. A WAF will add another layer of protection by allowing only legitimate traffic to access your site.
- Use advanced bot detection and mitigation
Bots are the primary tool used in carding attacks and testing card details at a large scale.
Advanced bot detection solutions can identify and block bot traffic in real time. They can also prevent suspicious transactions from occurring at your checkout.
“As of 2024, 55% of WooCommerce stores use bot protection to defend against automated threats like scraping, fake credit card testing, credential stuffing, and DDoS attacks.”
Services like BotGuard and PerimeterX specialize in advanced bot mitigation and can integrate with WooCommerce. These tools use machine learning to analyze user behavior, determining bots from real customers and blocking them as needed.
- Tokenize sensitive customer data
Tokenization replaces sensitive cardholder information with unique tokens that are useless if intercepted. By tokenizing data, your site minimizes the storage and transmission of sensitive information.
Many payment gateways, including Stripe and PayPal, offer tokenization services as part of their payment processing.
Therefore, implement a secure WooCommerce payment gateway with tokenization support to ensure card details are never stored directly on your site.
- Enable two-factor authentication (2FA) for admin access
Admin accounts are prime targets for attackers, and compromising one can lead to severe vulnerabilities. Two-factor authentication adds a layer of verification. It becomes harder for unauthorized users to access the backend.
Plugins like Wordfence, Duo, and Google Authenticator offer simple 2FA options that work well with WooCommerce. Enabling 2FA adds a powerful defense against unauthorized access, enhancing overall site security.
These advanced techniques provide complete protection for WooCommerce sites. Your store will also receive a strong security shield that can mitigate automated attacks and threats.
What to Do If a WooCommerce Site Is Under a Carding Attack?
Now, it’s the essential part. If you see that your store is under a WooCommerce carding attack, you must take action immediately to mitigate the losses.
We know that it’s a stressful and hectic situation to face. But you have no other way to skip it. So you have to face it.
To take everything under control, we have compiled a list of 6 immediate actions you can take.
1. Temporarily disable checkout
Pausing checkout stops the attack, giving you time to investigate without further damage. You can disable checkout by temporarily removing payment options or putting the site in maintenance mode.
There are several ways to do this. First, you can disable all the payment gateways if you navigate to WooCommerce>Settings> Payment. Then, users can complete the purchase.
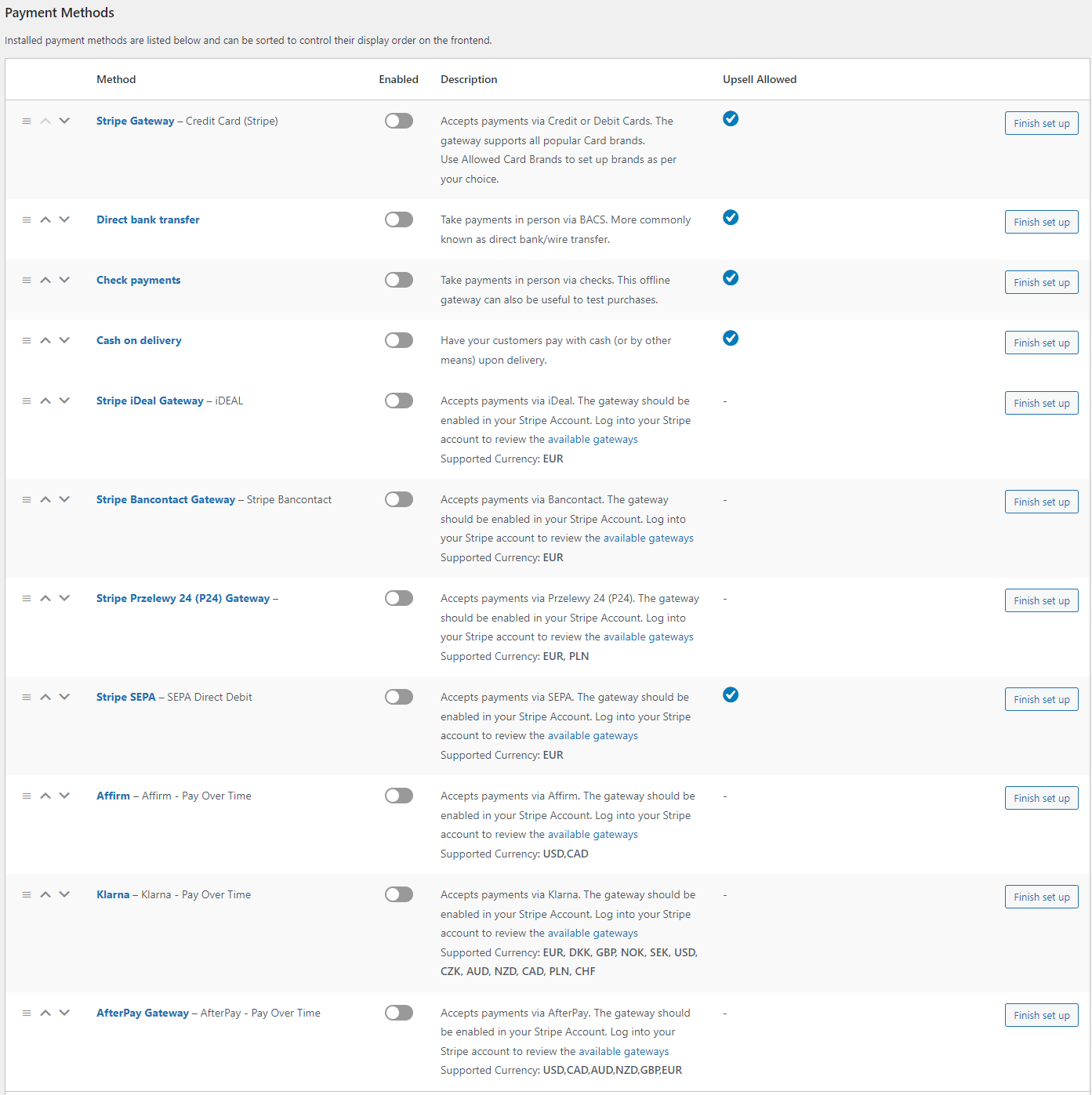
Your users will get this message on the checkout page. Thus they can not finish the purchase.
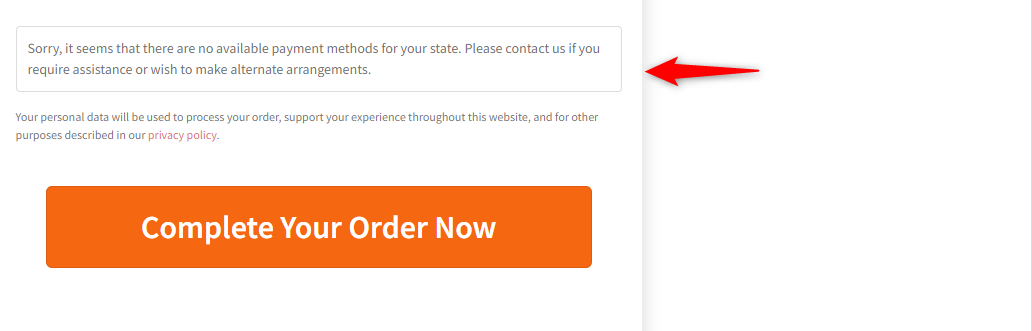
Also, if you’re using the FunnelKit Funnel Builder plugin for your checkout page, you can easily disable it from here. Just navigate to the store checkout page, and you can disable the checkout page.
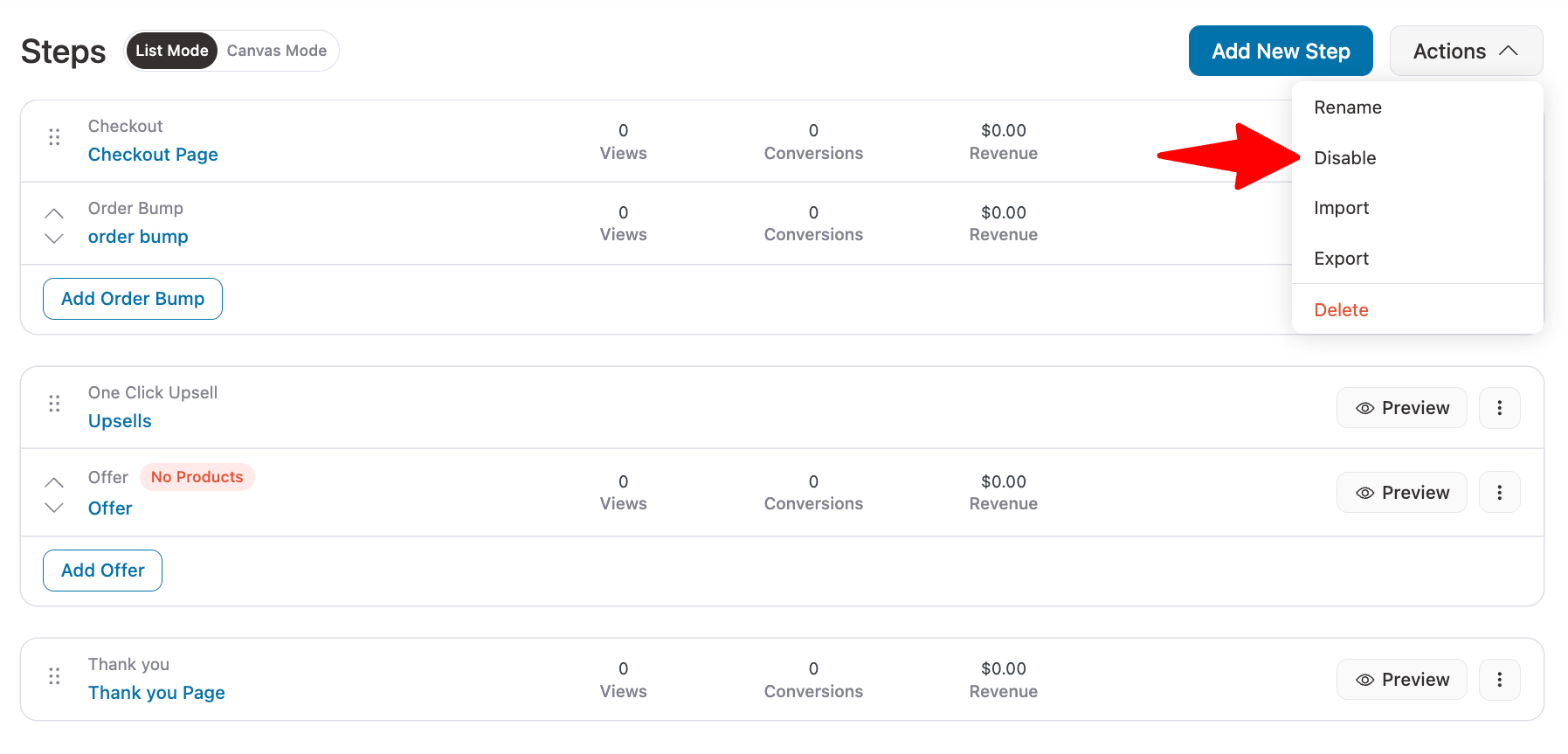
2. Disable checkout for logged-out users
You can immediately disable the checkout option for logged-out users. By default, there is no option, but you can do it using a simple code snippet.
Navigate to the theme editor section of your site. Find the functions. Php
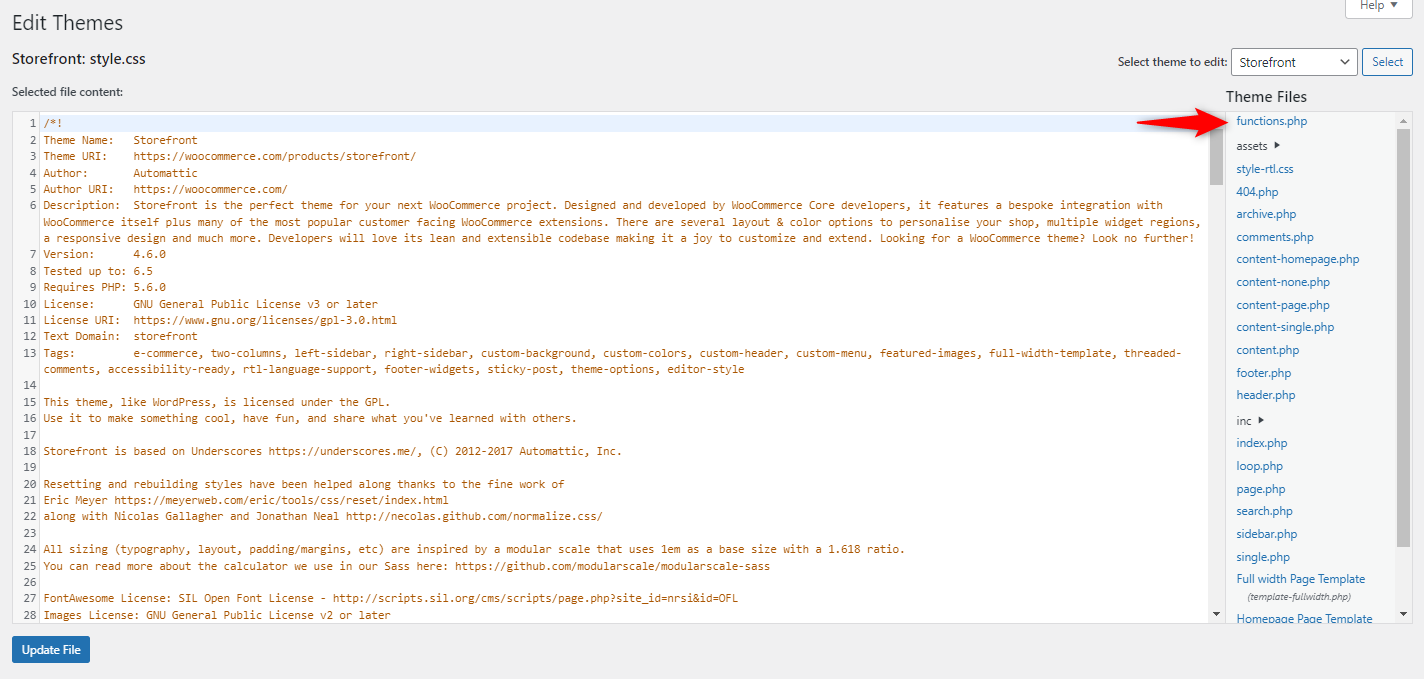
Simply copy this code and paste it here.
add_action('template_redirect', 'restrict_checkout');
function restrict_checkout() {
if (is_checkout() && !is_user_logged_in()) {
wp_redirect(home_url('/login-page'));
exit;
}
}
3. Hide the "Add to Cart" button site-wide
Another way you can take action is by deactivating the “Add to Cart” button on your store.
For instance, you have to be technical. Navigate to the theme editor tab from the Appearance.
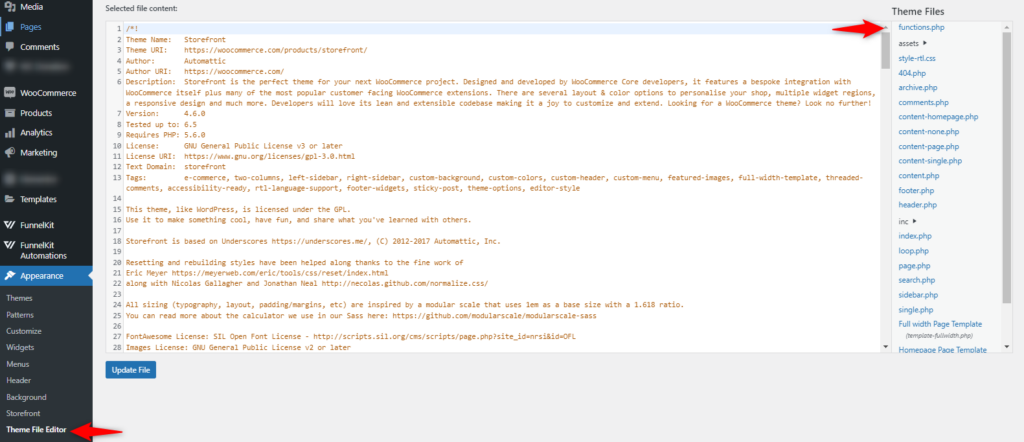
And then use this code here. And save it.
remove_action('woocommerce_after_shop_loop_item', 'woocommerce_template_loop_add_to_cart', 10);
remove_action('woocommerce_single_product_summary', 'woocommerce_template_single_add_to_cart', 30);4. Block suspicious IP addresses
Check your server logs to identify IP addresses generating high traffic on the checkout page. Blocking these IPs can cut off a significant portion of the bot traffic.
Many hosting providers and security plugins make it easy to ban IPs temporarily.
5. Review security settings and enable anti-bot tools
Take this opportunity to review your security settings.
Implement an anti-fraud plugin for WooCommerce, such as FraudLabs Pro or WooCommerce Anti-Fraud, to automatically monitor and block suspicious transactions.
6. Notify affected customers if necessary
If there’s a possibility that any customer information was exposed or misused, transparency is key. Let your customers know, advise them to monitor their accounts, and, if necessary, share steps they can take to secure their information.
So, these are the immediate actions you can take after encountering a card testing attack on your WooCommerce store.
Wrapping Up: Secure Your WooCommerce Store from Carding Attacks
Protecting your WooCommerce store from carding attacks is crucial to maintaining your business’s reputation and financial health.
By implementing effective fraud prevention strategies, like CAPTCHA, AVS, and rate-limiting, you can reduce the risk of these attacks significantly.
Additionally, using fraud detection plugins and regularly monitoring your store's activity will help you stay one step ahead of fraudsters.
Remember, security is an ongoing job. Stay updated, check your setup, and adjust as needed to avoid potential threats.
With your store well protected, you can shift your focus back to what matters most: growing your business and driving revenue. Tools like FunnelKit can help you enhance checkout security, optimize the customer journey, improve conversions, and create targeted sales funnels that boost your bottom line.
Ready to secure your store and take it to the next level?
Start implementing these proactive steps today and explore how FunnelKit can empower you to build a safer, more profitable WooCommerce store.

Editorial Team
February 27, 2026Expanding your WooCommerce store to a global audience is exciting, but delivering a truly seamless shopping experience across regions is not always simple. Shipping rates, taxes, and payment options often...

Editorial Team
February 27, 2026WooCommerce featured products let you handpick items from your catalog and showcase them prominently across your store, making them easier for shoppers to find. You can highlight your best-selling items...
Editorial Team
February 24, 2026The comparison of WooCommerce vs Shopify comes down to one choice. Control or convenience? WooCommerce is a free WordPress plugin where you own the code, pick your hosting, and customize...